Work
From
Home
Secure Access for Working-From-Home Employees
We have seen a shift over the last 2 decades around flexible working practices, allowing employees to “Work from Home” became an acceptable business practice for many organisations. This was compounded even further at the beginning of 2020 as COVID-19 Global Pandemic dramatically effected individual’s ability to travel and to mix with others, particularly in an enclosed environment.
Almost all Governments around the globe, encouraged individuals “work from home, where possible”. They placed restrictions on how many people could gather in a single location and this prohibited most office based employees from working in their traditional environments.
In this digital world, employee access is greatly simplified, using Cloud Services for application and data delivery has become the norm, while VPN (Virtual Private Network) is a standard offering in many Enterprise organisations.

Various Options for Authentication

Irrespective of how this digitial information is delivered, there is one common element across all solutions used today, in that users require a password to gain access to an environment. From cloud delivered apps, to virtual infrastructure solutions from organisations, such as Citrix, Microsoft and VMWare to VPN access, enabling secure communication channels provided by organisations such as Cisco, F5, Juniper. Users must use some form of security to gain access to each and every one of these environments.
Knowledge based authentication, such as passwords and PIN’s are inherently insecure, most of the data breaches we have seen have been through the misuse of user credentials, through shared credentials, phishing attacks or keyboard loggers. We have experienced a massive uptick in phishing attacks on Enterprise organisations since the beginning of the COVID crisis.
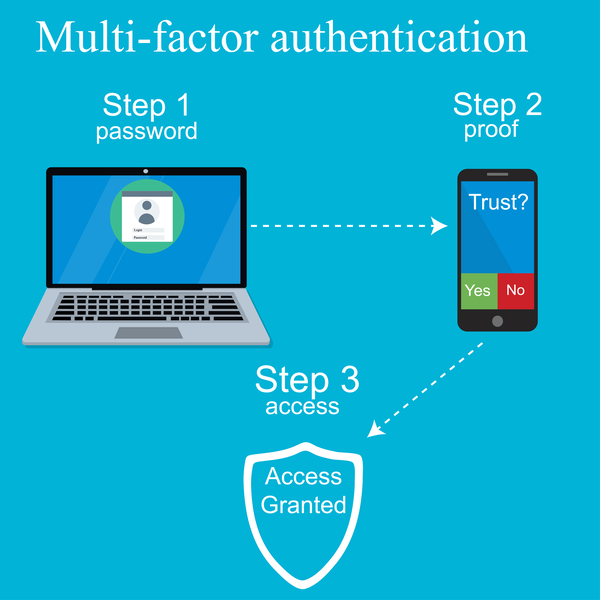
Organisations typically look to legacy MFA (MultiFactor Authentication) solutions on the market, to enhance security for their organisations and often to meet regulatory compliance for their sector. MFA products come in many shapes and sizes, from the original hardware tokens to software tokens, SMS or automated phone call delivering OTP (One Time Password) to users to add another level of security on top of the password.
Is Legacy MFA Enough?
Legacy MFA solutions, deliver a cumbersome user experience, add additional cost and complexity for organisations and are often only used for the point of entry such as VPN or Cloud service. The assumption being that MFA solution for user access at 9am in the morning should be enough security to trust that user remains the same user until they disconnect.
Working from home, organisations cannot physically see these users, they are not sat on the corporate trusted WiFi network and maybe they are not using a trusted corporate device, in essence there is a zero trust policy for working from home users. The VPN creates a trusted connection, your password permits access to protected environments, perhaps with a MFA to complement it, but these passwords and legacy MFA don’t prove user identity, it just proves a user has sufficient access to knowledge and a token to gain access and this is a massive security risk and concern for organisations, particularly with regulation around data access such as GDPR imposing heavy fines for data leaks to organisations.
VeridiumID Platform:
MFA and Everything Else You Need
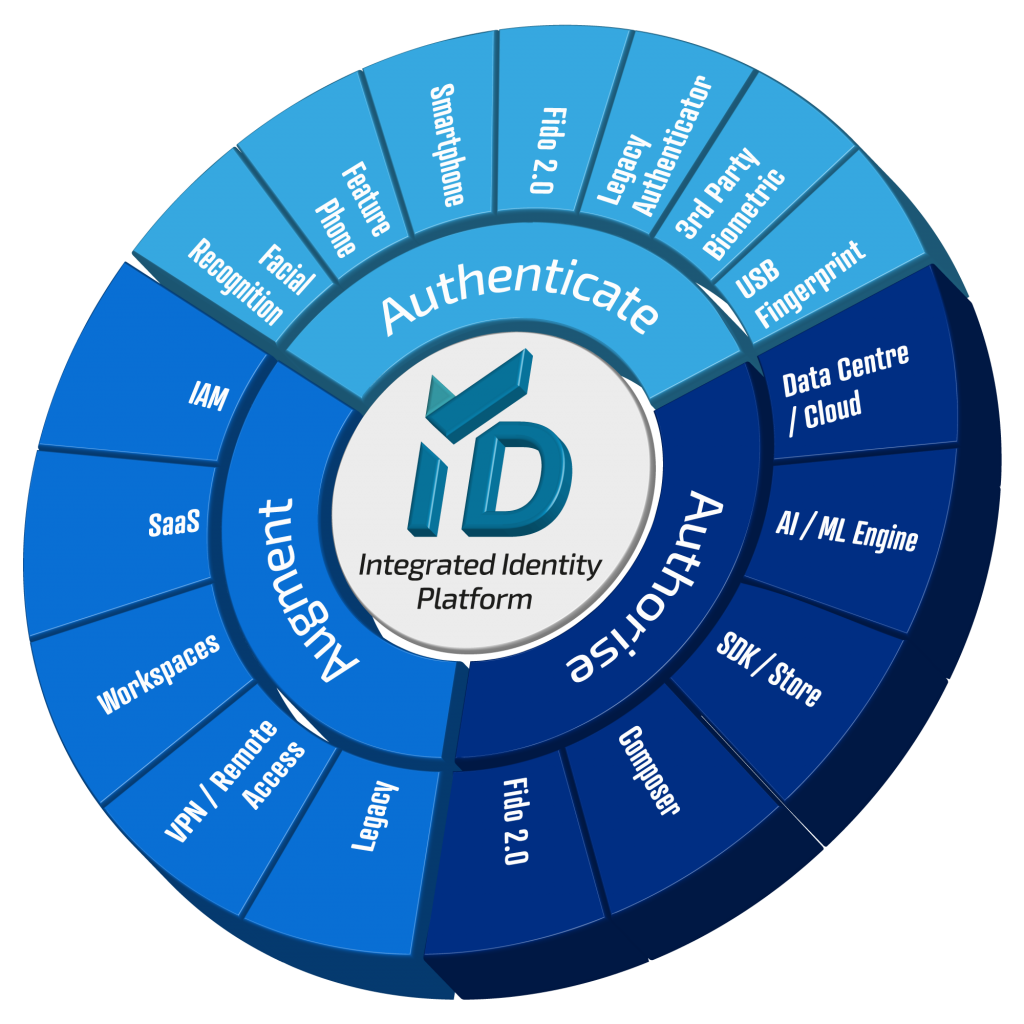
Veridium have focused on improving security for organisations. By delivering a passwordless solution to our customers, we have allowed IT Security to be increased. By removing the password, Veridium eliminate knowledge-based authentication, this means users cannot share credentials, phishing attacks cannot capture passwords (since they don’t exist), brute force attacks are eliminated, bad actors cannot guess a password that does not exist and keyboard loggers cannot capture password information.
Additionally, Veridium deliver an exceptional user experience. Users no longer have to reset passwords due to forgotten or lock out situations. Secure modern authentication is delivered to provide a simple, frictionless and strong authentication user experience.
Importantly, the Veridium solution works across an organisation’s entire application estate, no applications are left behind for Veridium passwordless authentication. From desktop logon, VPN access, VDI from Citrix, Microsoft or VMWare, Cloud, WEB, Mobile and even legacy applications, Veridium provide industry leading security in combination with exceptional user experience, all while driving down operational cost, through password and token elimination.
Combining possession, biometric and behavioural validation for user authentication is allowing Veridium customers to experience high levels of assurance that individuals accessing Corporate IT are who they claim to be, increasing security and meeting regulatory compliance.
Related Resources

Case Study
Global
Swiss Bank
Watch Now

Veridium Platform
in Action:
Workforce Authentication
Watch Now



