Some experts insist that security breaches in the digital sphere are inevitable. This is a sad thought, particularly coming from an expert, but it’s not unreasonable given companies’ largely lax attitude towards cybersecurity. Companies have shown an unwillingness and/or an inability to adopt the best security practices, even if they’re handling sensitive information.
But the fallout from a security breach doesn’t just cost a company time and money. It also costs the business its reputation. Words of concern don’t seem to be enough to create an attitude change, so perhaps concerning numbers will do the trick.
Hackers Are Causing More Security Breaches
Security breaches aren’t just due to hackers. They can also be the cause of system glitches or user error. But the share of security breaches that resulted from hacking is growing. From 2013 to 2017, there was a ten percent increase worldwide in breaches caused by hackers, rising to 47 percent. In the United States, that number has gone from 41 to 52 percent over the same time period.
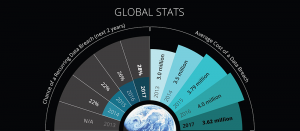
The Cost of Breaches Is Rising in the US
As hackers attempt to breach a company’s defenses, the average cost of a security breach in the United States has risen to $7.4 million. The cost has been steadily increasing over the past five years, even while the overall cost of a breach has been decreasing worldwide. However, the U.S. isn’t the only country plagued with these higher costs. The Middle East, Japan, and South Africa have all experienced similar increases over the past four to five years.
See how much the cost of data breaches has changed between 2013 and 2017 in our latest infographic.
These trends are troubling, especially considering that the chance of a recurring data breach has gone up to 28 percent– a six percent increase over four years. Organizations need to see these numbers, and then they must act. Knowledge is power, but there’s little power in knowledge if it doesn’t inspire action.
There are viable steps that any entity can take. Securing firewalls, improving encryption algorithms, and teaching employees practices regarding cybersecurity are good places to start. Ongoing discussions with your IT team are also crucial, as is staying abreast of hackers’ various tactics. This is where the process begins, but the important thing to remember is that if you’re doing it right, it never truly ends.